Phishing is a subject that we have written about several times before on this blog. However, as reported cases of UK cyberattacks continue to rise, and phishing attempts remain the most likely delivery method, we thought it may be useful to put out a timely reminder of what to look out for.
Criminals are becoming more creative and sophisticated in the construction of their attack emails, making it increasingly difficult to identify the phishing emails that manage to evade your spam filter and find their way to your inbox. With that in mind, we thought we’d run through some signs to look out for to help you identify a malicious email, be it personal or professional.
The very first step is to be alert at the moment when you receive an email that you weren’t expecting in the first place. If you don’t have a Mac, iPhone or iPad yet you receive an email from “Apple” saying you’ve just purchased something from the App Store – it’s probably bogus. If you’ve never had a friend or relative send you an impromptu gift in the past, I’m afraid it’s probably not your lucky day and unfortunately, there likely isn’t going to be a package waiting for you at the Post Office (after you’ve paid a small release fee).
Scam emails can often have poor grammar or spelling. Sometimes this is due to the content being translated from another language but oftentimes this is actually done by design. If you are alert enough to spot the errors then you are less likely to click on the link, and even more unlikely to give away any personal information or money if you do.
The emails often play on your emotions and/or could have an overwhelming sense of urgency to them. “Password Expired” or “Only the first 5 responders will get half price off” etc. It is ingrained within all of us to want to help others, or to be intrigued at the prospect of a fantastic bargain. Remember the old adage: if it’s too good to be true then it probably isn’t!
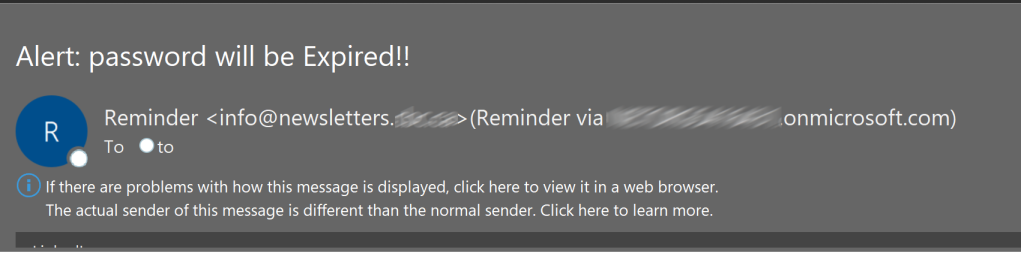
Malicious emails are designed to look like the real thing. Consider how you normally receive communications from an organisation. If they normally call or write you then why have they sent you an email with a number of attachments. Check the senders email address or hover over the links within the body to see which website the link is actually taking you to. If in doubt, ask someone for help. Use an alternate known method to contact the organisation who may have been spoofed to find out if they did indeed send you an email.
Given how realistic these emails can appear in the moment, you could be forgiven for falling for the initial hook. Hopefully these tips will help prevent you from becoming another cybercrime statistic.








.jpg?width=380&height=287&name=pexels-ron-lach-7928767%20(1).jpg)