Businesses beware! Cyber criminals are upping their game with an horrific new phishing scam - just in time for Halloween. Our customers have reported receiving what they believed were suspicious (spooky?) looking emails. Although these emails were not being flagged up by the default spam filters in Microsoft 365, it didn’t take us long to oust them as malicious attempts.
The attack starts with a phishing email sent by the attacker while posing as a company leader. Impersonating that individual and exploiting their authority, they attempt to get you to give up your personal mobile number. This is targeted approach, using information gained from social networks to identify leaders and their subordinates; hoping to find a vulnerable keen to make a good impression. Once you do, they use WhatsApp to bombard them with aggressive messages in the hopes of fooling them into making false purchases.
If you aren' familiar with the term 'phishing', read our article on what phishing is and how to avoid it here.
Why Cybersecurity Awareness Training Matters
Most businesses and establishments now offer some level of cybersecurity awareness training to their employees, students, or staff. Here’s where that short two-minute phishing awareness video you’re required to watch once a year finally proves its value. Phishing attacks remain the number one method used by cybercriminals to gain unauthorized access to a network. Fortunately, there are several tell-tale signs of a phishing email. Based on an actual phishing attempt, we have identified 4 common indicators that should immediately raise red flags when reviewing your inbox:
🔹A suspicious sending email address
🔹A sense of urgency in the message
🔹A change in writing style
🔹A forceful or aggressive tone
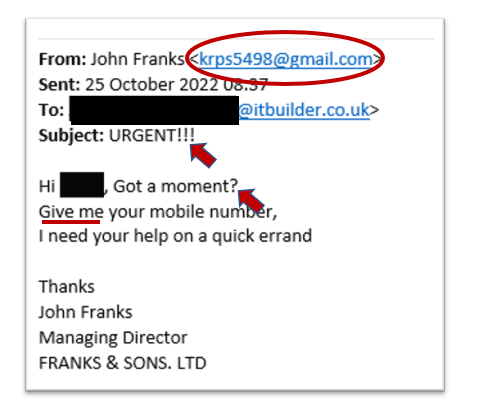
Everything about this malicious email is designed to make you act quickly - from seeing the falsified sender name in the “From” field to the urgency created in the subject line, short sentences, and assertive tone. The attacker relies on your quick reaction before you have time to properly analyse the email.
How Skimming and Psychology Aid Phishing Attacks
It works similarly to those passages where you can read text perfectly even when letters are jumbled, and to the bionic-style text in the paragraph above – which tricks the brain into skim-reading key information faster than usual.
Responding to the phishing email with your mobile number gives the attacker another way to attempt social engineering, and this time it targets you personally.
WhatsApp Phishing: When Personal Devices Are at Risk
WhatsApp phishing is increasingly used in the workplace, but it is still perceived as a personal platform. Once the attacker has your mobile number, they may contact you via WhatsApp, pretending to be the same business leader from the phishing email (in this example, “John Franks”). This tactic is clever because employees often have weaker security controls on personal devices, and a message on a personal app feels informal and trustworthy.
Similar to the email, the WhatsApp messages will often use the same psychological manipulation, with a forceful style and an even higher sense of urgency.
Why People Are Your Best Defence
Although these attacks may seem simple, the methodology relies on psychology to socially engineer employees. It exploits human tendencies to be helpful and cooperative. In the phishing email example, notice there are no attachments, no compromised accounts, no spoofed email addresses, no requests for login credentials, and no malicious links. The sending address is likely new with a neutral reputation, and traditional security software may not flag it. In short, people remain the most critical line of defence against phishing attacks.
Key Signs of a Phishing Attempt
Watch for these warning signs of a phishing attempt:
🔹A sense of urgency or pressure to act
🔹Spelling, grammar, or changes in writing style
🔹Unusual requests or tasks outside normal workflow
🔹Unfamiliar email addresses, websites, or links
🔹Offers that seem too good to be true
🔹Messages that play on emotions (fear, empathy, anger, sadness)
🔹Direct calls to action
Advanced Email Security and Awareness Training
Default spam filters are no longer sufficient protection. Where budgets allow, businesses should consider advanced email security solutions. Employee cybersecurity awareness training is no longer optional – it is a vital requirement for every organisation.
Contact us today to learn more about phishing scams, cybersecurity threats, and business protection strategies in an ever-evolving digital landscape.
And remember, when it comes to suspicious emails – if in doubt, report it!







-1.jpg?width=380&height=287&name=pexels-nataliya-vaitkevich-6919720%20(1)-1.jpg)
